Connect LogMeIn Resolve MDM to Microsoft Entra ID
To benefit from using automated workflows, LogMeIn Resolve MDM can be integrated with Microsoft Entra ID.
Results: Microsoft Entra ID is connected and ready to use. The connected status is shown on the Integrations page in LogMeIn Resolve MDM.
Register an application to integrate LogMeIn Resolve MDM with Microsoft Entra ID
Registering an application establishes trust between LogMeIn Resolve MDM and Microsoft Entra ID.
Register an application in Azure
Define permissions for an application in Azure
Generate a client secret in Azure
Troubleshooting common issues with Microsoft Entra ID integration
Some of the issues you might encounter with your Entra ID integration can easily be fixed.
Error: 400 – Bad Request
- Client ID (shown as Application (client) ID in Entra ID)
- Client secret (shown as Value, not Secret ID, in Entra ID)
- Tenant (shown as Directory (tenant) ID in Entra ID)
To correct this error, ensure that you use the credentials provided in the application that you created and you are not using the tenant properties of your Entra ID account. For more information, see Connect LogMeIn Resolve MDM to Microsoft Entra ID.
Error: 401 – Unauthorized
- Client ID (shown as Application (client) ID in Entra ID)
- Client secret (shown as Value, not Secret ID, in Entra ID)
- Tenant (shown as Directory (tenant) ID in Entra ID)
To correct this error, ensure that you use the credentials provided in the application that you created and you are not using the tenant properties of your Entra ID account. For more information, see Connect LogMeIn Resolve MDM to Microsoft Entra ID.
Error: 403 – Forbidden
An Error: 403 - Forbidden message can appear during application registration if the configured permission type is not set to Application.
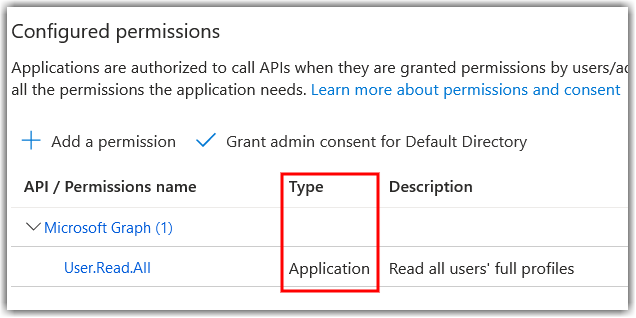
Correctly configured permission type in Azure
This error can also occur if you do not select Grant admin consent for Default Directory for the User.Read.All and Group.Read.All permissions while defining permissions for your application.
To correct this error, follow the steps in Define permissions for an application in Azure.
Users are not visible in LogMeIn Resolve MDM
- In Entra ID, navigate to .
- If the Email column is not visible in the table, select and enable the Email column.
- Open the user entry and on the Overview tab, select Edit properties at the top.
Note: While the User principal name might look like an email address, it is not sufficient to link the user entry to LogMeIn Resolve MDM.
- Navigate to the Contact Information tab and enter the user's email address in the Email field, then select Save.
Insufficient privileges during filter testing
When testing an Entra ID user query filter, you might encounter the error "Insufficient privileges. Please check that all necessary app permissions have been assigned in Entra ID.". To correct this error, check that the Group.Read.All and User.Read.All permissions are granted in Entra ID. If they are missing, add them, then grant admin consent for both.
For more information on granting permissions, see Define permissions for an application in Azure.
Issues with Workflows when Entra ID is connected
- Your Workflows suddently don't work even though they used to.
- You receive an Error: 401 – Unauthorized message during filter testing.
- The Action log shows an error for a workflow.
To resolve this issue, generate a new client secret in Azure as described in Generate a client secret in Azure.
